- The world we live in is highly connected and digitally exhaustive. Today, social networks have become one of the main communication channels. Of the 7.6 billion humans on the earth 3.6 billion are online.
- Today, social networks have become one of the main communication channels. Within relatively short social media has empowered people and connected them.
- But, at the same time, they have also provided platforms for some decidedly unhealthy and destructive behavior. There are many problems like bullying, cybercrime, copyright issues, security threats and social unawareness among others.
- In the year 2016, there were a total of 758 million online attacks worldwide, which amounts to around 2 million in a single day. Every organization, be it big or small, has been the victim of cyber-attacks.
Different types and forms of cyber attacks
- Bots: Bots and fake followers are a big concern in the social media environment. These programs target specific hash tags and work by auto-commenting and auto-liking in order to attract followers who are mostly fake bot accounts.
- Bots were developed primarily for companies to engage with their users automatically for increasing customer engagement. However, bots are now being used much beyond their harmless cause and are misused for manipulating a conversation to creating a mirage of someone’s personality and much more.
- In this age of misinformation, bots possess the power to hijack a conversation, troll someone, promote propaganda and even cause security issues.
- Terrorist Attacks: Terrorists have always sought attention and this is what they receive from the social media. Social media spread the horror far and wide and unknowingly amplify the chaos that the terrorists intend to spread.
- Extremists use the social media to make an impact. They even use it to recruit, propagate and to connect. The rapid spread of false information through social media is among the emerging risks identified in Global Risks Report.
- Social media sites have now initiated reporting procedures that allow users to flag any kind of content that supports terrorism which can be then removed. Also, the social networking sites today are playing an important role in counter-terrorism operations. For example, Assam State Police opened a cell to monitor social media and keep track of the spread of rumors.
- Cyber Security Challenges: Some new threats have also come up like organized cybercrime, cybercrime trading, smishing (phishing with SMS), hacktivism (hacker with activism) etc. Another type of attack that is rising recently is distributed denial of service (DDoS) attacks.
- Here the intruder is not interested in actually stealing one’s information but in bombarding his/her server with unnecessary traffic thereby crashing it.
- Mobile Technologies: There are different types of personal information on one’s mobile. This raises an important question – what if a hacker is able to build one’s digital profile by collecting all these censored information and the data from the third-party apps and use it against that person?
- Internet of Things (IoT): It is another such challenge posed by the new technology whereby every object we use is equipped with the capabilities to identify, locate, sense its surrounding, compute and communicate.
- Ransomware: This ransom demanding malware is a virus which gets into your computer, either when you download an attachment containing the virus or when you visit any such website and click on a link. Once it gets into your computer, it starts to encrypt all your files thereby rendering them useless. The only way to unlock your files is to get a secret key from the hacker by paying a ransom.
- Big Data: We are actually living in exponential data times. In Just 60 seconds 149,513 emails can be sent, 3.3 million FB posts can be made, 3.8 million Google searches can be performed. As a result, it has become lot easier to hack people using social engineering techniques and make them reveal information rather than using tools and technology.
Protection against cyber-crime
- Avoiding malicious downloads done by mistake.
- Avoiding malicious installs done by mistake.
- Preventing from being a victim to Man In The Middle Attack(MITM)
- Protection from phishing.
- Protection from damage that trojan horses may cause. Some Trojan Horses are built in a way that the majority of the code is for doing useful and seemingly innocent things while a small portion does something nasty like acting as backdoor or escalating privileges.
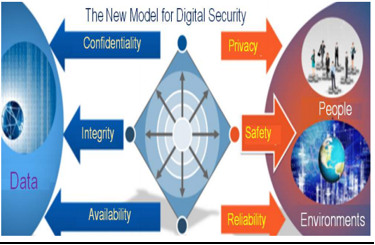
Need for a secure cyber-space
- Digital literacy is a broader concept that consists of developing new skills and knowledge which provides awareness and advanced level thinking skills. It is extremely essential to be digitally literate for appropriate utilization of digital information resources.
- It is the responsibility of each one of us to understand and use the cyberspace sensibly and responsibly. This will definitely ensure that the netizens are not only techno-savvy and socially existent but also digitally safe.
Related Articles