

29th June 2022 (6 Topics)
Context
‘Hermit’ is the latest sophisticated spyware in the news, and it is believed to have targeted iPhones and Android devices in Italy and Kazakhstan.
About
- Hermit’s deployment – the spyware has been developed by an Italian vendor called RCS Lab.
What is Hermit?
- Hermit is a spyware on the lines of Pegasus by NSO Group.
- According to the report, Google and Lookout have confirmed that Hermit is a commercial spyware that known to be used by governments with victims in Kazakhstan, Italy and northern Syria.
What exactly does it do on a device?
- Once installed on a device, it can record audio on the device, carry out unauthorised calls, and carry out many unauthorised activities.
- The spyware can steal stored account emails, contacts, browser bookmarks/searches, calendar events, etc.
- It can also take pictures on the device, steal device information such as details about applications, the kernel information, model, manufacturer, OS, security patch, phone number, etc.
- It can also download and install APK (the app software files on Android) on a compromised phone.
- The spyware can also upload files from the device, read notifications, and take pictures of the screen. Because it can gain access to the root or the ‘privilege’ access of an Android system.
- According to the researchers, the spyware can silently uninstall/reinstall Telegram. Except the reinstalled version is likely a compromised one.
- It can also steal data from the old app. For WhatsApp, it can prompt the user to reinstall WhatsApp via Play Store.
So, once Hermit has been deployed to a phone, it can control and track data from all key applications.
How did Hermit get deployed on Android and iOS devices?
- Sophisticated spyware such as Hermit and Pegasus cost millions of dollars in licensing fees, and these are not simple operations.
- It’s not like common malware targeting regular users.
- And in the case of Hermit, it appears the operations used were complex.
- According to Google’s TAG team, all campaigns started with a unique link sent to the victim’s phone. When the user clicked, the page installed the application on both Android and iOS.
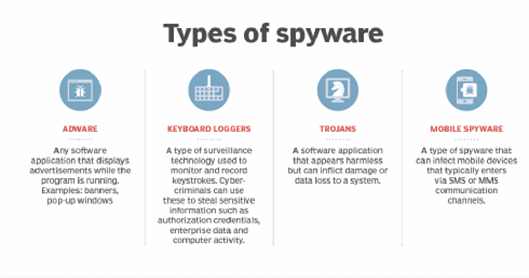
Spyware
- Spyware is the term given to a category of software which aims to steal personal or organisational information.
- Spyware is a type of malicious software or malware that is installed on a computing device without the end user's knowledge.
- It invades the device, steals sensitive information and internet usage data, and relays it to advertisers, data firms or external users.
|
Other terms related to it
|
More Articles


