

1st September 2025 (15 Topics)
Context:
There has been a sharp surge in malicious APK-based cyber frauds in India, with Parliament informed of a 900% rise in cybercrimes between 2021 and 2025.
Nature of Fraud:
- Malicious APK files on Android devices function like .exe files on Windows. Fraudsters circulate fake apps mimicking government portals (PM-Kisan, tax refund, electricity boards, banks) to steal credentials and intercept OTPs.
Impact:
- The National Cyber Crime Reporting Portal logged 12,47,393 cybercrime cases in the last six months. Telangana Cyber Security Bureau reported ?779.06 crore losses (Jan–July 2025), with daily financial losses of ?10–15 lakh.
Operation:
- 60–70% of malicious APKs are developed in India (Delhi NCR, Meerut, Jharkhand, etc.), while 30–40% trace back to the U.S., U.K., and China. Telegram and dark web serve as key distribution channels.
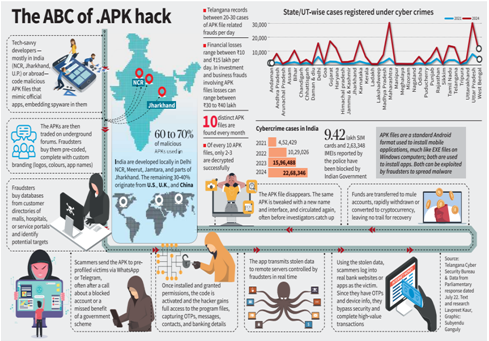
Targeting Method:
- Fraudsters buy leaked datasets containing names, numbers, and income details, enabling tailored scams. High-income professionals (doctors, bankers, real estate agents) are prime targets.
Technical Modus Operandi:
- Fraudulent APKs remain dormant during installation, bypass antivirus scans, then harvest data (contacts, location, banking details) and transmit it encrypted to external servers.
Investigation Challenges:
- Only 20–30% of APKs are decrypted successfully. Financial trails often end in mule accounts or cryptocurrency, making masterminds hard to trace. Google has recently removed ~50 malicious apps based on reports.
Policy Relevance:
- Highlights urgent need for stronger cyber hygiene, stricter app vetting by intermediaries, enhanced digital literacy, and cross-border cybercrime cooperation.
More Articles


